INTRODUCTION
The biggest myth about wireless is that it is not secure. Wireless is only as secure as it is made. Most wireless APs come with several security settings. Many devices default to the WPA (Wireless Protected Access). This security protocol is based on EAP (Extended Authentication Protocol) and uses both a pass key and a group key to maintain a secure environment. WPA outlines the use of several encryption protocols, TKIP (Temporal Key integrity protocol), and in version 2 of WPA, AES (Advanced Encryption Standard). TKIP has become less secure over the years but AES remains secure.
WPA2
WPAv2 uses CCMP (Counter Mode Cipher Block Chaining Message Authentication Code Protocol) which is part of the AES encryption suite. This protocol creates secure messages that cannot be cracked without knowledge of the passkey and group key used to encrypt the packets. The group key is sent to all members of a BSS and could be sniffed by a third party, but the key itself is constantly renewed and encrypted. WPA also uses MIC (Message Integrity Check) as checksums to ensure that messages being sent by a client are truly secure. This is designed to combat a man in the middle attack. When several MIC failures occur, the BSS disconnects all clients for a blackout period and voids all authentications. This makes it so all unauthorized parties are wiped from the BSS, meaning they will have to begin the hacking process. While this is good in theory, and could indeed help prevent attacks on users data, with AES being so secure, there is not much need. Indeed, this could be used as a way to DoS (Denial of Service) attack a WLAN. If frames are constantly sent with invalid MICs , the whole network would be brought down.
WPS AND WLAN HACKING
Another security flaw wireless has is WPS (Wireless Protected Access). The idea of WPS is to allow a user to gain access to a WLAN without entering the password. This makes it easy to connect to a WLAN and leaves the password secure. The issue with this technology is that tools exists that can extrapolate the AES passkey from attempting a WPS connection. No matter what level of security that may be present, someone could get in. This is a vital issue that is trying to be worked out by 802.11 developers. Their current solution is using MFP (Management Frame Protection) which is designed to encrypt all frames in a BSS including those sent before authentication. How it works is, at the discovery step of authentication, the client and the AP negotiate an encryption to use before using the security of the BSS, that way frames like the WPS frames could not be sniffed and used to extrapolate the passkey. The issue with this is that anyone can connect to these networks and both sides can decrypt, so this would be still vulnerable to WPS hacking tools.
CONCLUSION
The truth is that wireless is secure and not as vulnerable as many think. It has its flaws, but all systems do. Hacking techniques like WPS hacking requires both WPS enabled and 7 hours of time. Wireless is a very secure system that is built to ensure the user’s information is secure.
QOS
QoS (Quality of Service) is important in any networking standard and 802.11 is no exception. IEEE 802.11e outlines how QoS is implemented within a WLAN. This standard outlines priority traffic categories that allow for priority transmissions. This is accomplished using a MAC layer Hybrid Coordination Function (HCF), made up of two parts known as Enhanced Distributed Channel Access (EDCA) and Hybrid Coordinated Channel Access (HCCA). HCCA is another HCF that combines EDCA and a Point Coordinated Function (PCF) to create a more efficient QBSS (QoS BSS). EDCA creates the idea of traffic categories (TC) to create a transmission hierarchy. The TCs range from best effort to voice, each TC being higher than another, making it so streams that require more access to the WM (Such as video) get the access they need.
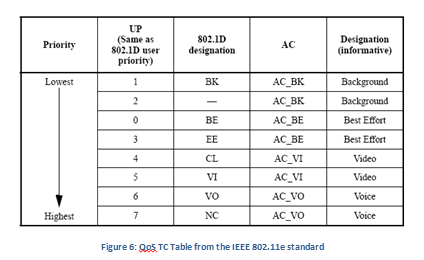
This adds to the DCF that most wireless devices use, having clients reserve a transmit opportunity (TXOP) for a given TC. HCCA adds the idea of AP control over these TC; it adds the PCF that can override EDCA using what is called admissions control. Each TC has an admissions control that determines the priority of the stream within the TC.
QoS ensures equal access to the WM and while watching a video or using VOIP, it ensures that the data will reach the user. EDCA is designed to be tweaked by setting what is called the EDCA parameter set. This set of parameters determines key aspects of the QBSS such as whether admissions control is enabled and how long a TC has of a TXOP. In theory, QoS will help create a WM that allows important data streams to have priority access to the WM. This means that when a user is downloading a file over wireless and another is watching a video, the user watching the video will not lose part of his video because the other is downloading something.
Stay tuned for the next blog, Wireless Reliability - Packet Aggregation
To read more from Jackson Corson, check out his other blogs: Wireless Reliability, Wireless Reliability - Modulation, Wireless Reliability - Channel Bounding and Wireless Reliability - Guard Intervals
Jackson Corson, Wireless Technician
